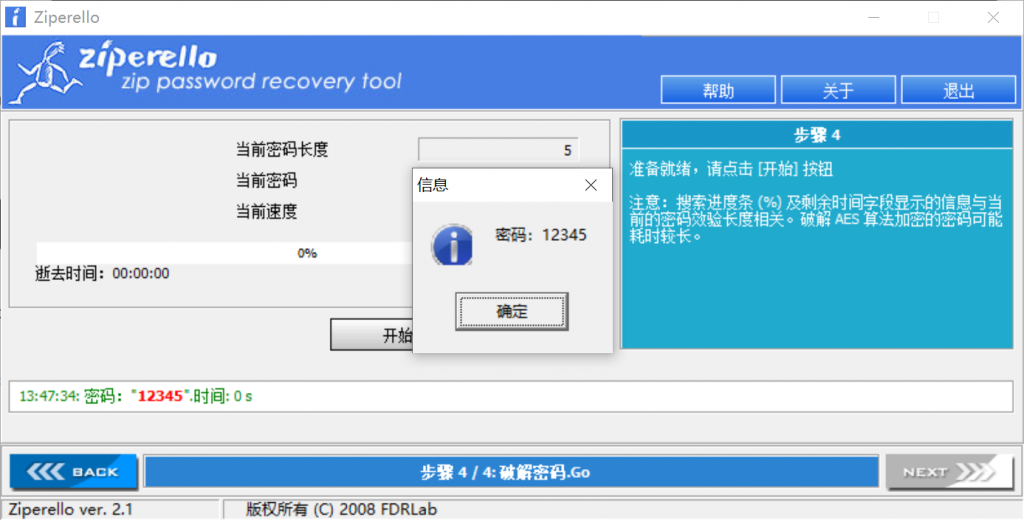
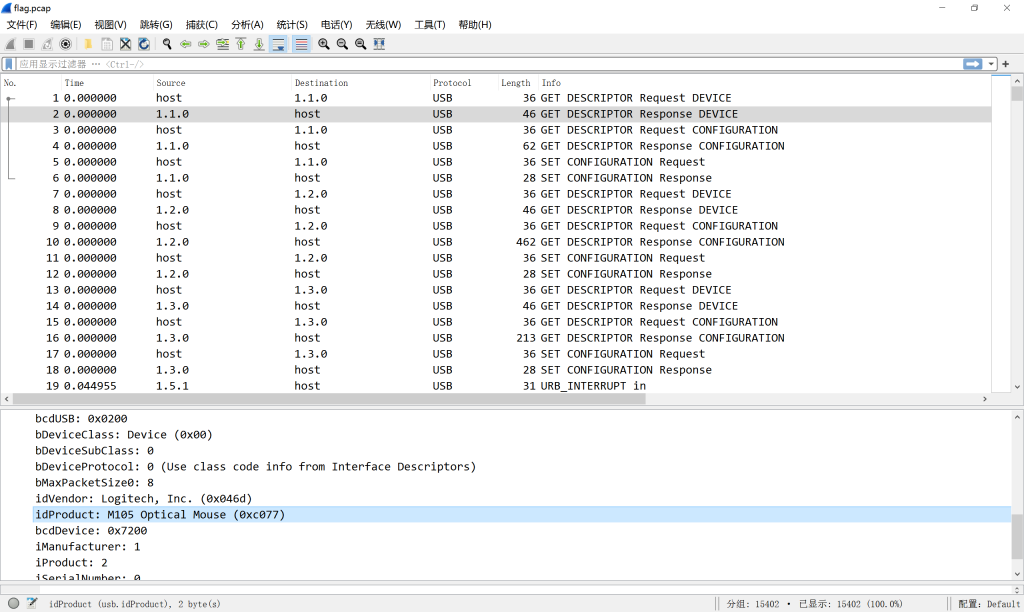
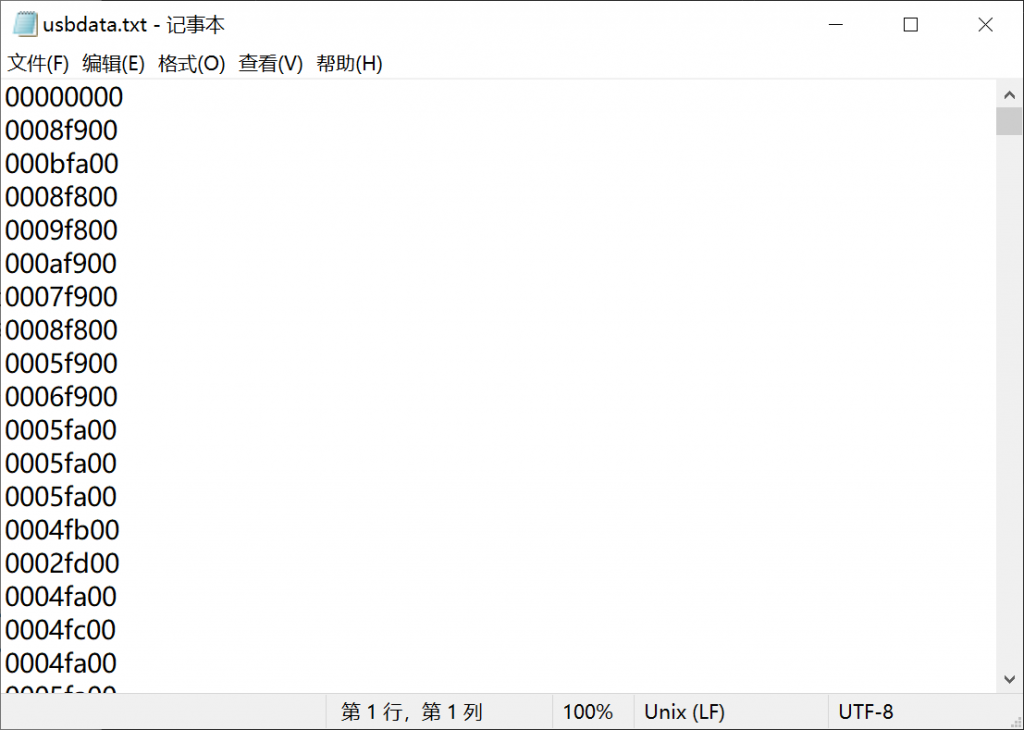
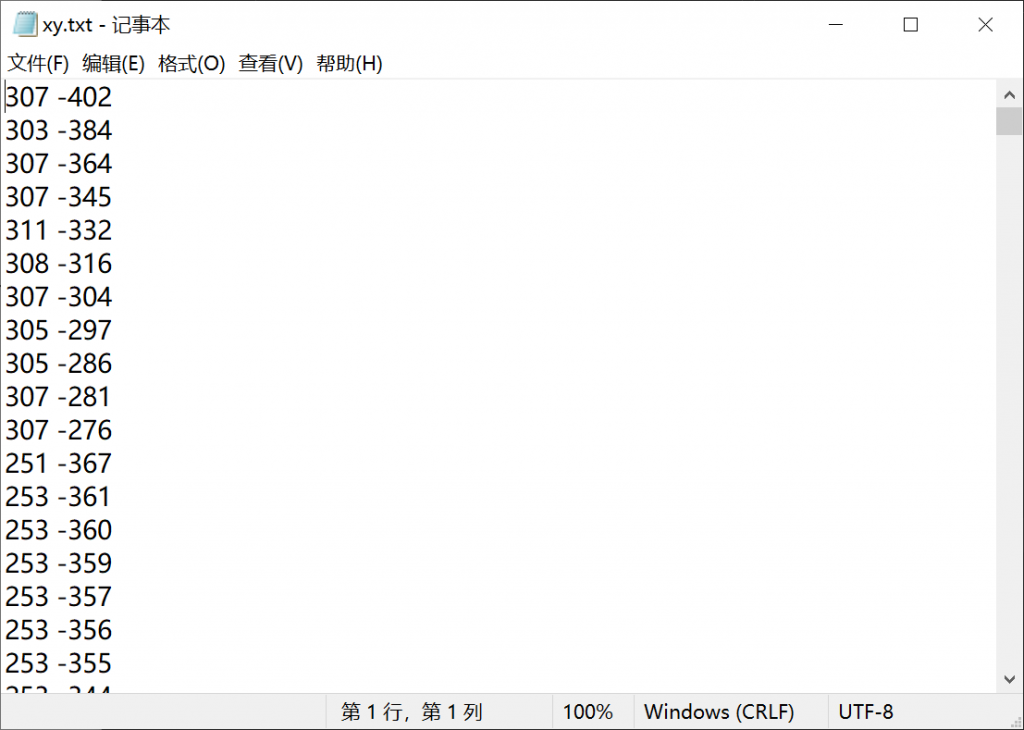
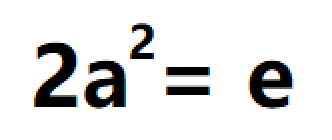1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
|
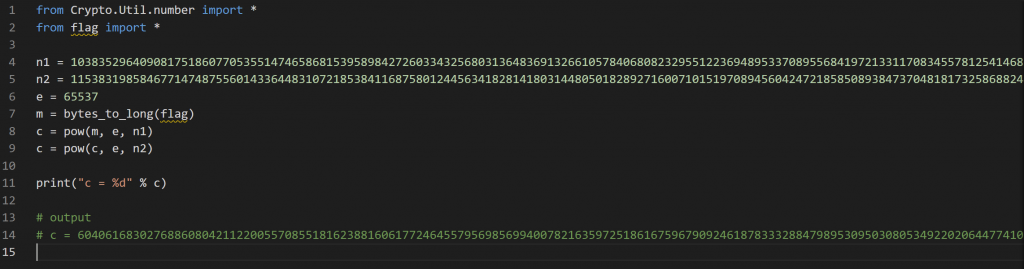
import sys
import hashlib
from z3 import *
import socket
import time
otherIP = '192.168.39.182'
otherPort = '2378'
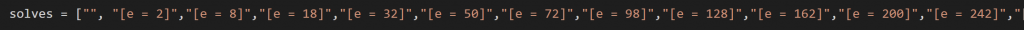
solves = ["", "[e = 2]","[e = 8]","[e = 18]","[e = 32]","[e = 50]","[e = 72]","[e = 98]","[e = 128]","[e = 162]","[e = 200]","[e = 242]","[e = 288]","[e = 338]","[e = 392]","[e = 450]","[e = 512]","[e = 578]","[e = 648]","[e = 722]","[e = 800]","[e = 882]","[e = 968]","[e = 1058]","[e = 1152]","[e = 1250]","[e = 1352]","[e = 1458]","[e = 1568]","[e = 1682]","[e = 1800]","[e = 1922]","[e = 2048]","[e = 2178]","[e = 2312]","[e = 2450]","[e = 2592]","[e = 2738]","[e = 2888]","[e = 3042]","[e = 3200]","[e = 3362]","[e = 3528]","[e = 3698]","[e = 3872]","[e = 4050]","[e = 4232]","[e = 4418]","[e = 4608]","[e = 4802]","[e = 5000]","[e = 5202]","[e = 5408]","[e = 5618]","[e = 5832]","[e = 6050]","[e = 6272]","[e = 6498]","[e = 6728]","[e = 6962]","[e = 7200]","[e = 7442]","[e = 7688]","[e = 7938]","[e = 8192]","[e = 8450]","[e = 8712]","[e = 8978]","[e = 9248]","[e = 9522]","[e = 9800]","[e = 10082]","[e = 10368]","[e = 10658]","[e = 10952]","[e = 11250]","[e = 11552]","[e = 11858]","[e = 12168]","[e = 12482]","[e = 12800]","[e = 13122]","[e = 13448]","[e = 13778]","[e = 14112]","[e = 14450]","[e = 14792]","[e = 15138]","[e = 15488]","[e = 15842]","[e = 16200]","[e = 16562]","[e = 16928]","[e = 17298]","[e = 17672]","[e = 18050]","[e = 18432]","[e = 18818]","[e = 19208]","[e = 19602]","[e = 20000]"]
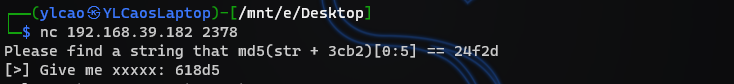
def md5Col(one, two):
for i in range(1048576):
text = hex(i).replace('0x', '')
if md5(text + one)[0:5] == two:
print(md5(text + one))
return text
def md5(text):
content = text.encode('ansi')
md5hash = hashlib.md5(content)
md5 = md5hash.hexdigest()
return md5
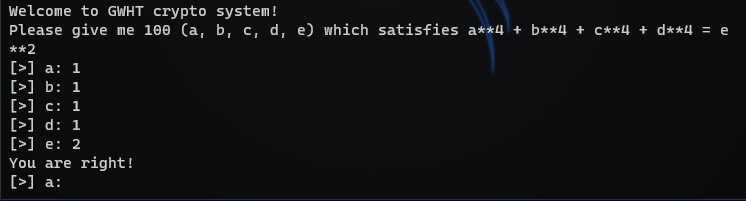
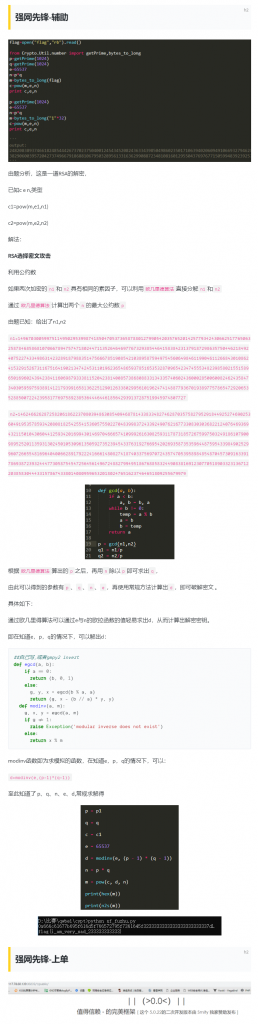
def col(n):
a = Int('a')
b = Int('b')
c = Int('c')
d = Int('d')
e = Int('e')
solve(2*n**2 == e)
if __name__ == '__main__':
client = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
client.connect((otherIP, int(otherPort)))
mess = client.recv(1024).decode('utf-8')
print(mess)
one = mess[36:40]
two = mess[50:55]
print(one, two)
print(client.recv(1024).decode('utf-8'))
firstAnswer = md5Col(one, two)
if firstAnswer == None:
exit()
print(firstAnswer)
client.send(firstAnswer.encode('utf-8'))
print(client.recv(1024).decode('utf-8'))
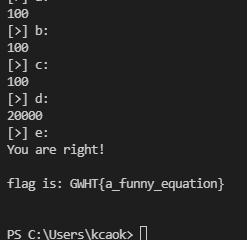
for i in range(1, len(solves)):
A = B = C = D = str(i)
E = solves[i].replace('[e = ', '').replace(']', '')
print('show : ' + A, B, C, D, E)
print(client.recv(1024).decode('utf-8'))
time.sleep(0.2)
client.send(A.encode('utf-8'))
print(A)
print(client.recv(1024).decode('utf-8'))
time.sleep(0.2)
client.send(B.encode('utf-8'))
print(B)
print(client.recv(1024).decode('utf-8'))
time.sleep(0.2)
client.send(C.encode('utf-8'))
print(C)
print(client.recv(1024).decode('utf-8'))
time.sleep(0.2)
client.send(D.encode('utf-8'))
print(D)
print(client.recv(1024).decode('utf-8'))
time.sleep(0.2)
client.send(E.encode('utf-8'))
print(E)
print(client.recv(1024).decode('utf-8'))
print(client.recv(1024).decode('utf-8'))
print(client.recv(1024).decode('utf-8'))
print(client.recv(1024).decode('utf-8'))
|